ArcGIS Online OAuth with ServiceStack
Esri recently released support for authenticating users and applications using OAuth 2 on their new developer site. In this post we will look at adding a provider to an existing web site built using ServiceStack to see how you can integrate your ArcGIS Online (AGO) users with another web application.
The ArcGIS documentation covers user and app logins. We will be focusing on user logins since app logins will most likely be transparent to end users via a proxy or the like. To get started you should sign in to ArcGIS for Developers with your subscription or developer account and in your applications choose new application and set the details.
As we want to use OAuth we also need to set the Redirect URI, this should match the location of the provider. For testing my application looks like
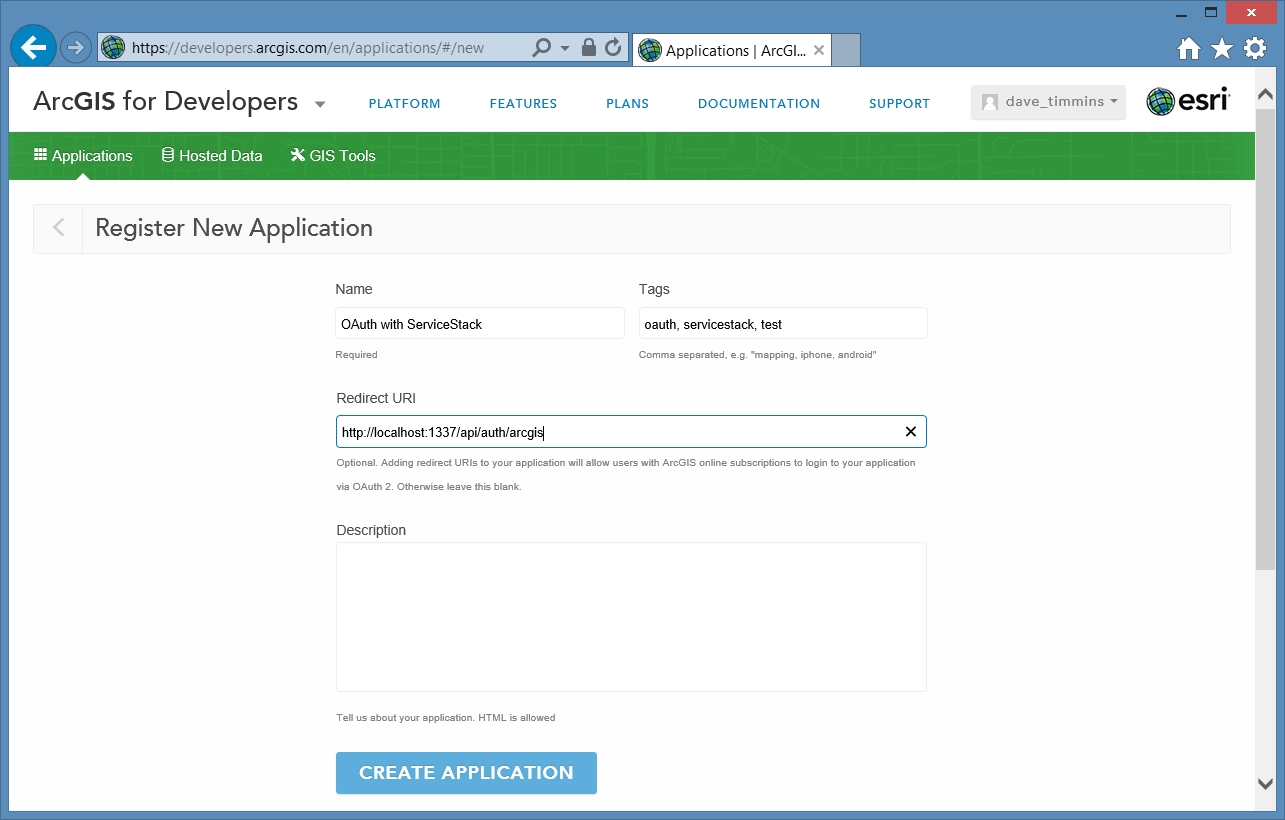
once created we can select API Access from the sidebar to get the Client ID and Secret to use when authenticating. Make sure to note these down but do not share them publically
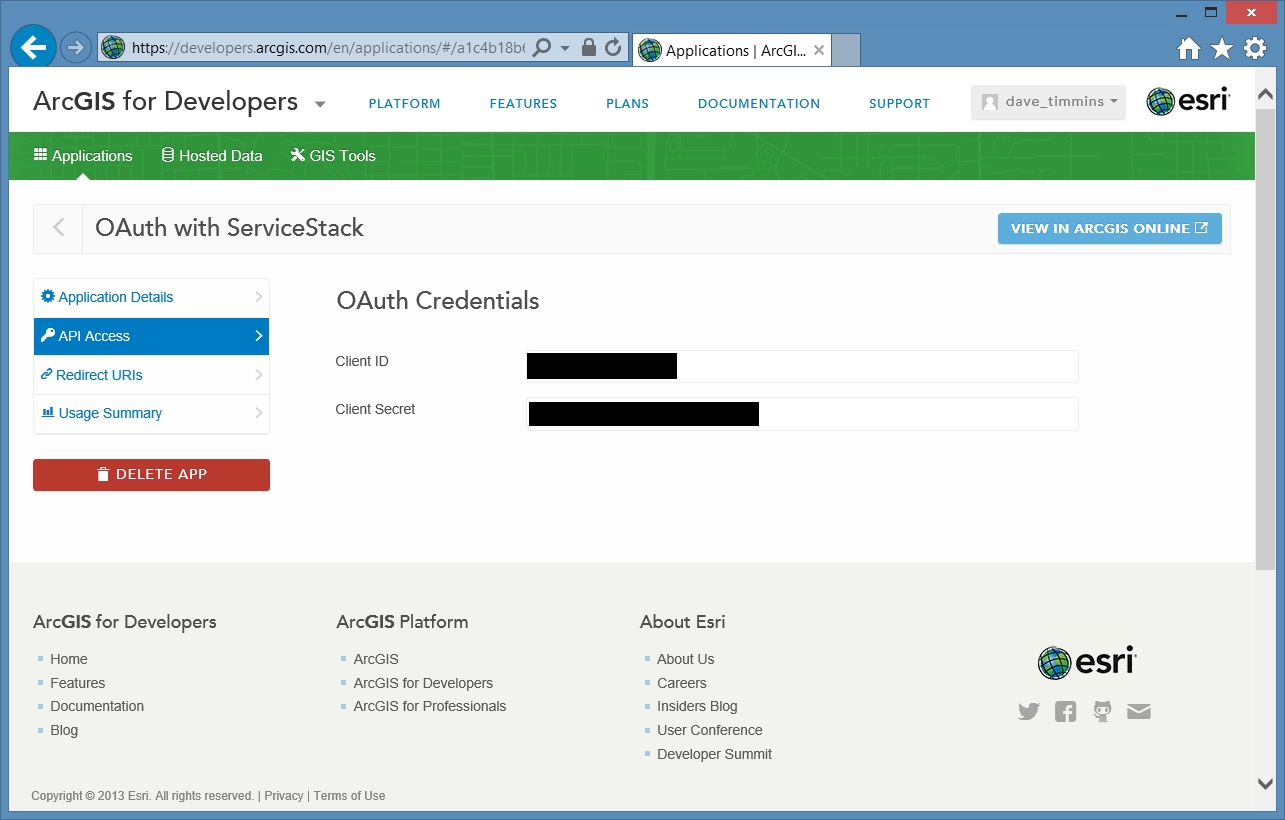
Now that we have our application configured with AGO we are ready to code the OAuth provider. To speed testing up I used the ServiceStack Social Bootstrap template as this already has similar functionality so it is just a matter of adding the new provider. ServiceStack makes this very easy thanks to its excellent documentation and wealth of sample code.
The details for parameters and urls to call are on the ArcGIS website so I’ll let you look at the code rather than waffling on about it but in a nutshell we are getting verification from AGO that the user is who they say they are and then getting some additional user information via the ArcGIS Portal API.
There is already an OAuthProvider base class for us to inherit from so we’ll base our implementation on that. The only other steps we need to follow are to register our new authentication provider with ServiceStack by including it as an authentication method in our AppHost
|
|
then add the configuration application settings to our web.config to pass through the Client ID and Client Secret that we created earlier. The convention the ServiceStack uses for these is
|
|
where arcgis is the name defined in our provider. Though as with pretty much everything in ServiceStack the key names can be configured.
Finally you will need some UI to show the user a link to click and choose to sign in with ArcGIS. This will be a link to points to the same place as the redirect url we configured when adding our application to AGO. Hopefully someone will make a nice icon for people to embed in their sites.
In Index.cshtml under Views/Shared
|
|
When you run the app and click on the sign in with ArcGIS link you will be redirected to AGO where you can now enter your AGO account credentials.
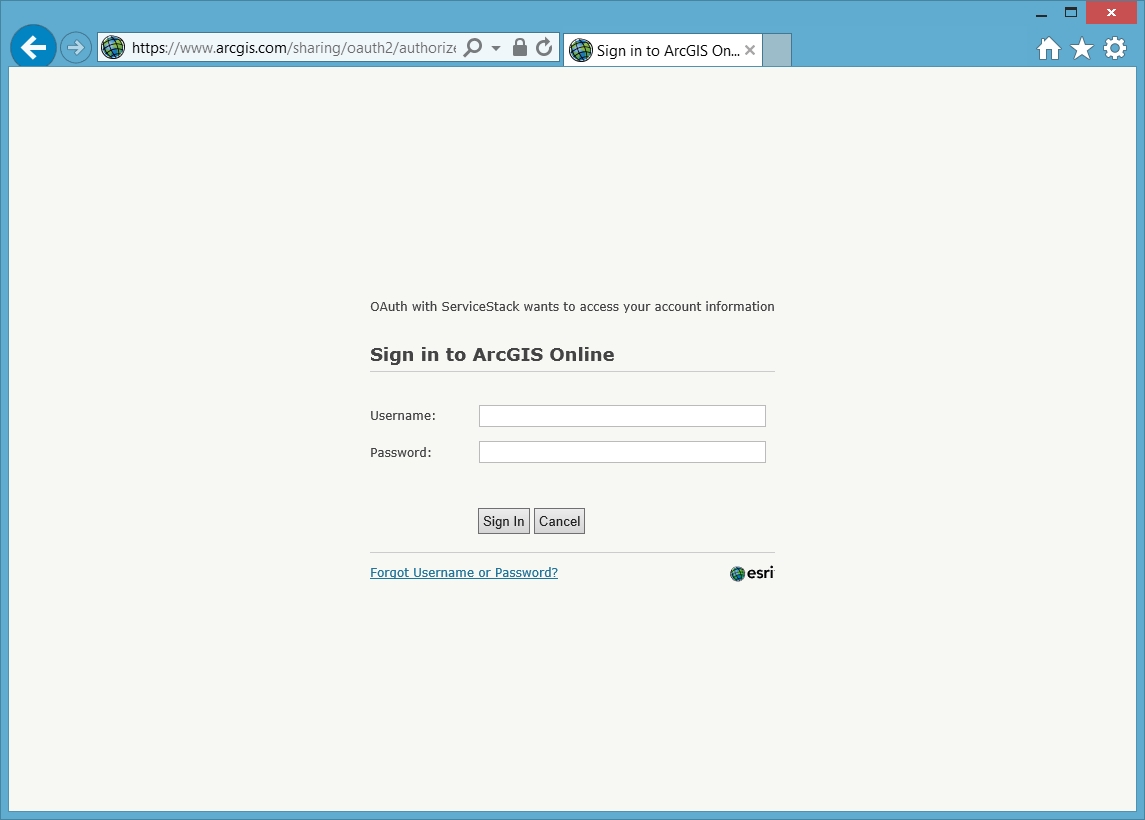
The full code for the ArcGISAuthProvider is listed below. Thanks for reading.
|
|